Ironscales Allow File List
Ironscales Allow File List - Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing authorized. Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. Think very carefully before you add domains to the allowed domains list. To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. Never add your own accepted domains or common domains (for.
Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. Think very carefully before you add domains to the allowed domains list. Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing authorized. To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. Never add your own accepted domains or common domains (for.
To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing authorized. Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Think very carefully before you add domains to the allowed domains list. Never add your own accepted domains or common domains (for.
IRONSCALES™ Starter™ for Phishing Simulation Testing Tutorial YouTube
Never add your own accepted domains or common domains (for. Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access.
IRONSCALES Ranks No. 875 on the 2022 Inc. 5000 Annual List Business Wire
To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. Think very carefully before you add domains to the allowed domains list. Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. Are you looking to optimize.
IronScales Quarantine Release Request YouTube
To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. Are you looking to optimize your organization's email security with ironscales but need help figuring out where.
IronScales The Evolution of Email Security 2014 YouTube
Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. Think very carefully before you add domains to the allowed domains list. In cybersecurity, whitelists, also known as allowlists, serve as a.
Think very carefully before you add domains to the allowed domains list. Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage. Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? To ensure that the campaign is successfully received by employees.
IronScales Report Email Outlook Desktop YouTube
Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing authorized. To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to.
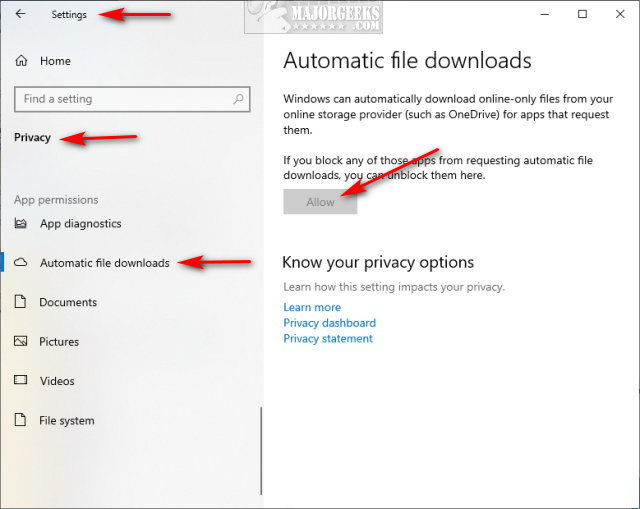
How to Allow or Block Automatic File Downloads in Windows 10 & 11
Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Never add your own accepted domains or common domains (for. Think very carefully before you add domains to the allowed domains list. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing authorized. To.
Bela Silva,
Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. Never add your own accepted domains or common domains (for. In cybersecurity, whitelists, also known as allowlists,.
File under “The Trump GOP just makes s*^t up whenever it suits” https
Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Never add your own accepted domains or common domains (for. Think very carefully before you add domains to the allowed domains list. Ironscales allows you to define your trusted sender's ip, domain, or address and your trusted domain's links or webpage..
IronScales Stealth Network Services
Never add your own accepted domains or common domains (for. Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Think very carefully before you add domains to the allowed domains list. To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant.
Ironscales Allows You To Define Your Trusted Sender's Ip, Domain, Or Address And Your Trusted Domain's Links Or Webpage.
To ensure that the campaign is successfully received by employees in the organization, make sure to add the relevant domains and ips to the. In cybersecurity, whitelists, also known as allowlists, serve as a proactive access control mechanism by explicitly allowing authorized. Are you looking to optimize your organization's email security with ironscales but need help figuring out where to start? Never add your own accepted domains or common domains (for.